
The year: 2020. The date: Oct 12. The time: 10.10 a.m. Several Mumbaikars had already reached their offices and resumed work. Some were in elevators. But most of them were on board the Mumbai-bound local trains on the way to their workplaces.
Suddenly, the elevators stopped midway. The Mumbai locals, also known as the financial capital’s lifeline and carried more than 7.5 Mn commuters every working day in pre-coronavirus times, came to a halt. Barring the NSE, the BSE and the Mumbai international airport, almost all operations in the city had to stop for 5-12 hours due to the tripping of the 400 KV Padgha-Kalwa transmission line that supplies power to Mumbai.
Maharashtra state energy minister, Nitin Raut, seconded the reports that cited Chinese forces behind the cyberattack. The Indian government later stated that National Critical Information Infrastructure Protection Centre (NCIIPC) informed through mail on Feb 12 about threat by Red Echo (Chinese state-sponsored group) through malware Shadow Pad that “Chinese state-sponsored threat Actor group known as Red Echo is targeting Indian Power sector’s Regional Load Dispatch Centres along with State Load Dispatch Centres. All IPs and domains listed in NCIIPC mail have been blocked in firewalls at all control centres. Log of firewall is being monitored for any connection attempt towards listed IPs & domains. Additionally, all systems in control centres were scanned & cleaned by antivirus.
Since then, the state government and the Centre have continued to hum and haw on the issue. Union power minister R.K. Singh has also played down the involvement of Chinese hackers by saying, “The grid failure was caused by a human error and not due to cyberattack.”
But it was not a random incident out of the blue. It is worth noting that Chinese hackers have also attempted Mumbai-like attacks in other parts of the country. So far, over 10 power sector assets have been attacked by Red Echo. This include Delhi state load despatch centre, Mumbai Port Trust, NTPC’s Kudgi power plant and southern regional load despatch centre in Karnataka, VO Chidambaranar port in Tamil Nadu, Telangana load despatch centre, eastern regional load despatch centre in West Bengal load despatch centre and northeastern regional load despatch centre in Assam.
CERT-In successfully thwarted one such attack in Telangana in 2019. However, it is just one among the lakhs of attempts made every year. Stuart Solomon, the COO of the US-based cyberintelligence firm Recorded Future that published an analysis on China’s Red Echo Group’s role in the cyberattack on Maharashtra’s Power System Operation, said that the Chinese state-sponsored group (Red Echo) had been seen to systematically utilise advanced cyberintrusion techniques to quietly gain a foothold in nearly a dozen critical nodes across the Indian power generation and transmission infrastructure.
Think of other national and private organisations that had fallen victim to cyberattacks. The Defence Research and Development Organisation (DRDO), Indian Space Research Organisation (ISRO), the website of the defence ministry, the Kudankulam Nuclear Power Plant (India’s largest nuclear power plant), the Nuclear Power Corporation of India (NPCIL), or public and private-sector banks like the State Bank of India (SBI), HDFC Bank and the ICICI Bank — all these and more had been targeted by hackers in the past, raising multiple questions regarding their cybersecurity measures.
In the past, the Chinese PLA Unit 61398 and the APT22 Group, North Korean Lazarus Group and many others had tried to systematically sabotage India’s defence and offence mechanism as well as its infrastructure.
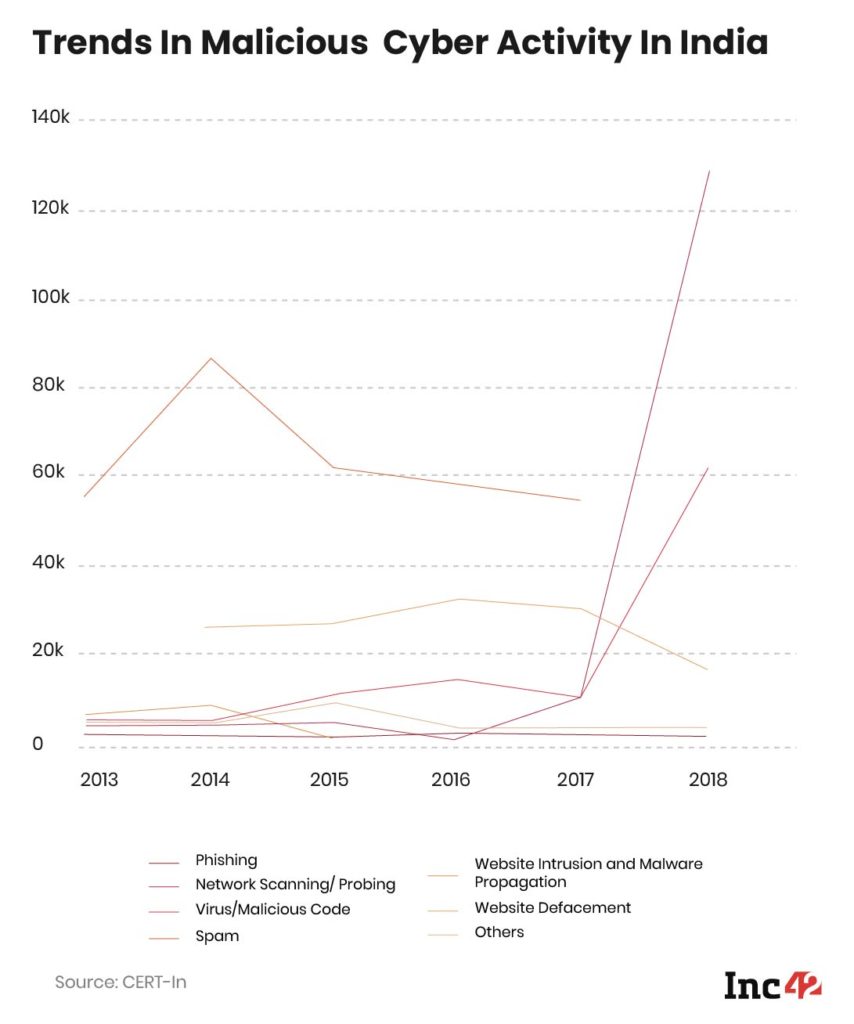
According to CERT-In data, 336 websites belonging to central ministries, departments and state governments were hacked between 2017 and 2019. And in 2019 alone, India witnessed 3.94 Lakh cybersecurity breaches.
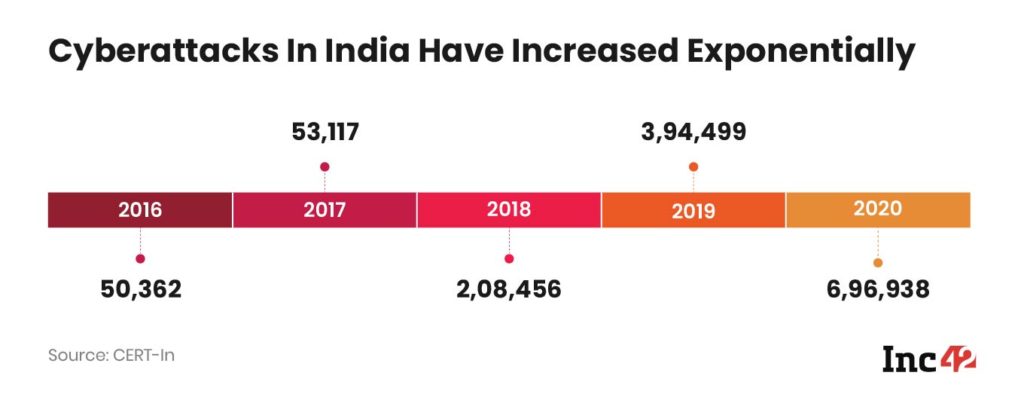
But this number skyrocketed in 2020 and saw a 75%+ rise to 6,96,938. Despite numerous initiatives at the state and central levels, India has failed to rise to the rapidly soaring cybersecurity challenge due to certain inherent vulnerabilities and inadequate preventive and deterrent mechanisms (more on that later).
Several experts do not agree with this metric (number of attacks), though. Pointing out that the numbers can be misleading, Pukhraj Singh, a cybersecurity expert who earlier worked for the National Technical Research Organisation (the cyberarm of India’s foreign intelligence agency, Research and Analysis Wing), says, “Analysing cyberattacks at a scale, like in terms of metrics, is misleading. Because we do not know what the definition of a cyberattack is. If someone is probing your networks and collecting, say, basic information, how is it to be classified? Putting it as a cyberattack may not be right”
Are ‘Chinese Attackers’ Targeting Critical Indian Infrastructure?
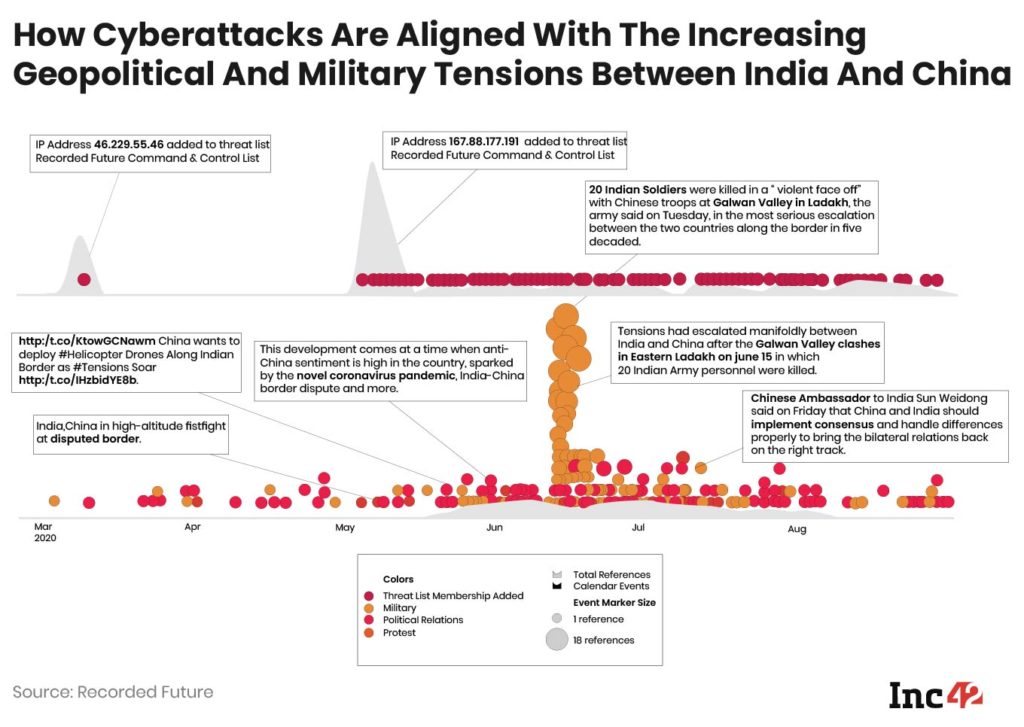
Before we deep-dive into the action required, an analysis of the current environment will help one understand why these attacks have gone up multifold. In a recent study, Recorded Future has analysed how these attacks are correlated with the geopolitical conflict between India and China. Referring to the Chinese attack on the Indian army at the Galwan Valley and India banning most of the Chinese apps following the skirmishes,, the study states how growing tensions between the two Asian neighbours have led to rising cyberespionage activities by both sides.
“For example, we observed the suspected Indian state-sponsored group Sidewinder target Chinese military and government entities in 2020, in activity overlapping with (the) recent Trend Micro (a cybersecurity firm) research. In the lead-up to the May 2020 skirmishes, we observed a noticeable increase in the provisioning of PlugX malware C2 infrastructure, much of which was subsequently used in intrusion activity targeting Indian organisations,” says the report.
In fact, Red Eco is just another mask for the People’s Liberation Army in China, much like the APT22, APT41 and the North Korean cybercrime group Lazarus whose association with China is well-reported.
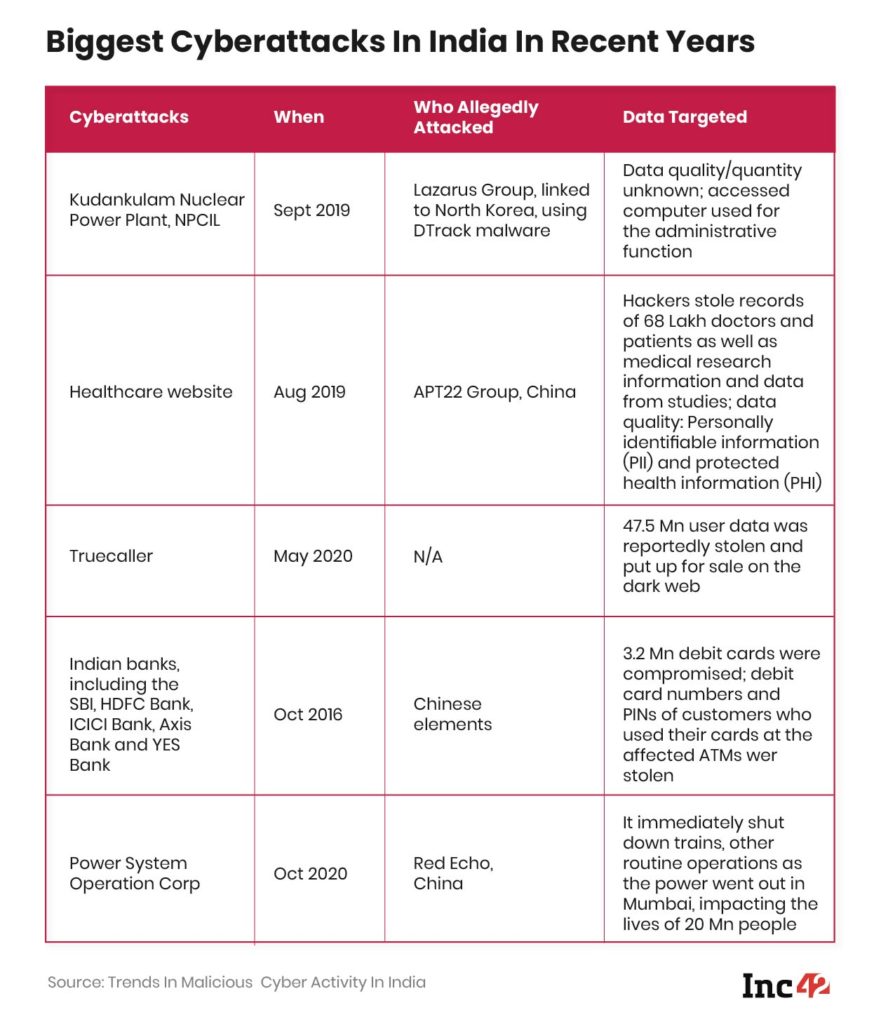
“The war is no more at the Himalayan or Indo-Pakistan borders but has been extended and intruded to India’s internal affairs – critical infrastructure, be it India’s banking system in 2016, which saw the world’s largest reissue of debit cards, or India’s nuclear power plant in 2019 or stealing of 68 Lakh doctors’ and patients’ data in 2019,” says a cybersecurity expert currently working with one of the cyberintelligence agencies of the government.
On average, more than 30 cyberattacks are daily reported in the country’s power sector alone. CERT-In and NCIIPC have been successful in preventing most of them. But in September, 2019 hackers managed to insert a malicious software programme in an NPCIL administrative network for the first time. The potential extent of damage can be easily understood as the agency is responsible for running India’s nuclear reactors.
According to reports, the malware called DTrack, which was placed in the NPCIL’s admin network, used to gather internet search history from the browser installed on the machine besides collecting local OS registry data such as registered owner, registered organisation, date of installation, current user and a list of currently active processes on the machine. Finally, it scanned for information regarding the network on which the affected machine was.
Besides power, petroleum and gas, banking and healthcare are two other critical elements of the Indian infrastructure. And both sectors had come under huge cyberattacks, allegedly by Chinese hackers.
The 2016 cyberattack on Indian banks is considered one of the biggest attacks on banking systems globally. As part of an organised cybercrime, more than 3.2 Mn debit cards’ details, including personal identification numbers or PINs were stolen. Victims also reported unauthorised usage of their card data from Chinese locations.
The worst-hit among the banks were the SBI, YES Bank and Axis Bank. According to reports, the breach originated in the malware introduced in Hitachi Payment Services systems, enabling fraudsters to steal information, which led to stealing funds. Hitachi provides ATM, point-of-sale (PoS) and other financial services to financial institutions and merchant aggregators.
The damage was immediately brought under control as banks started blocking cards when malicious usage was suspected. The Reserve Bank of India later released more stringent guidelines for transactions made through credit and debit cards.
A significant portion of the U.S. espionage and mass surveillance stories have been put out in the public domain by Edward Snowden, WikiLeaks founder Julian Assange and others. However, this is not the case with China despite several alleged espionage cases and cybercrimes by Chinese Advanced Persistent Threat (APT) groups, including PLA units 61398 and 61486, Red Echo and more. “There is much more that has not been exposed yet. For instance, after 61398 got exposed, we came to know about 61486. It is just the tip of the iceberg, we know very little about China-sponsored cyberattacks,” says a cybersecurity expert who works with the Indian government agencies on the condition of anonymity.
“Take Lazarus Group’s hackers, for instance. Many of them are not from China although all of them are, in fact, officially trained in Shenyang, China. It is China that micromanages their work and arranges their accommodation,” he adds.
The Lazarus Group has been infamous for some of the biggest cyberattacks, including the WannaCry ransomware attack, which affected more than two Lakh computers worldwide, damaging hundreds of millions of assets. The group is also suspected to be behind the cyberattack on India’s largest nuclear power plant.
While PLA Unit 61398 and Unit 61486 and Shadow Network were directly associated with the Chinese government in the past and acted as the PLA’s espionage arm, more APT groups have been created now to extend these espionage activities in other critical areas where the PLA does not want to be directly involved. For example, APT41 carries out Chinese state-sponsored espionage activity in addition to financially motivated activity, potentially outside of state control. According to California-based cybersecurity company FireEye’s analysis, since 2013, APT41 has targeted organisations involved in the research, development and sale of computer components used for machine learning, autonomous vehicles, medical imaging and the consumer market. The group has also targeted companies providing motherboards, processors and server solutions for enterprises.
In fact, one can actually identify a pattern behind the major cyberattacks happening across the globe. In 2012, Trend Micro published a report that found Gu Kaiyuan, a Tencent employee, behind a massive data espionage programme being carried out in India, Japan and Taiwan.
Although the Chinese government disavowed Gu, according to The New York Times, the techniques and the victims point to a state-sponsored campaign. Gu apparently had recruited students to work on Sichuan university’s research involving computer attacks and defence.
According to the IT security company Trend Micro’s report, a malicious document containing “information on India’s ballistic missile defence programme” was used to lure potential victims into opening it. This document contained malicious code that exploited a vulnerability in Microsoft Office and dropped a trojan virus onto a compromised system so that it would connect to a command-and-control (C&C) server operated by the LuckyCat hackers.
A similar modus operandi was often followed, resulting in Huawei, ZTE, DJI and a slew of other Chinese companies facing a phaseout in major global markets, including India, the US, the UK, Australia, the EU and other countries. The U.S. Department of Commerce has recently added as many as 33 Chinese companies to this list.
Speaking about the number and the impact of major cyberattacks in recent times, Adam Palmer, chief cybersecurity strategist at the US-based cyber exposure firm Tenable, said that from January through to October 2020, there were 730 publicly disclosed events resulting in 22 Bn+ records exposed worldwide. Around 35% of the breaches analysed by Tenable were linked to ransomware attacks, resulting in tremendous financial cost, while 14% of the breaches resulted from email compromises. One of the overarching themes of the threat landscape in 2020 was that threat actors relied on unpatched vulnerabilities in their attacks and chained together multiple vulnerabilities as part of their attacks.
What Are India’s Recent Cybersecurity Measures
Just like other countries, India has taken measures on multiple levels as cyberwarfare involves collusion, conspiracies, collisions and undeclared trade wars between the parties involved. We already saw a demo of the same as India amended its FDI policies to control increasing Chinese direct investments, banned 300+ Chinese apps and kickstarted a nationwide campaign ‘vocal for local’, restricting China’s fast-growing front-end and backend access to Indian markets.
Also, given the defence and commerce implications in the drone space, the government has strict regulations that completely restrict the free run of DJI drones. Drones will also require certain hardware changes as these will be monitored when flying within the Indian territory.
These are only a few instances of the policy-level measures taken against China when the Asian giant upped the ante and entered a war-like situation against India and other nations.
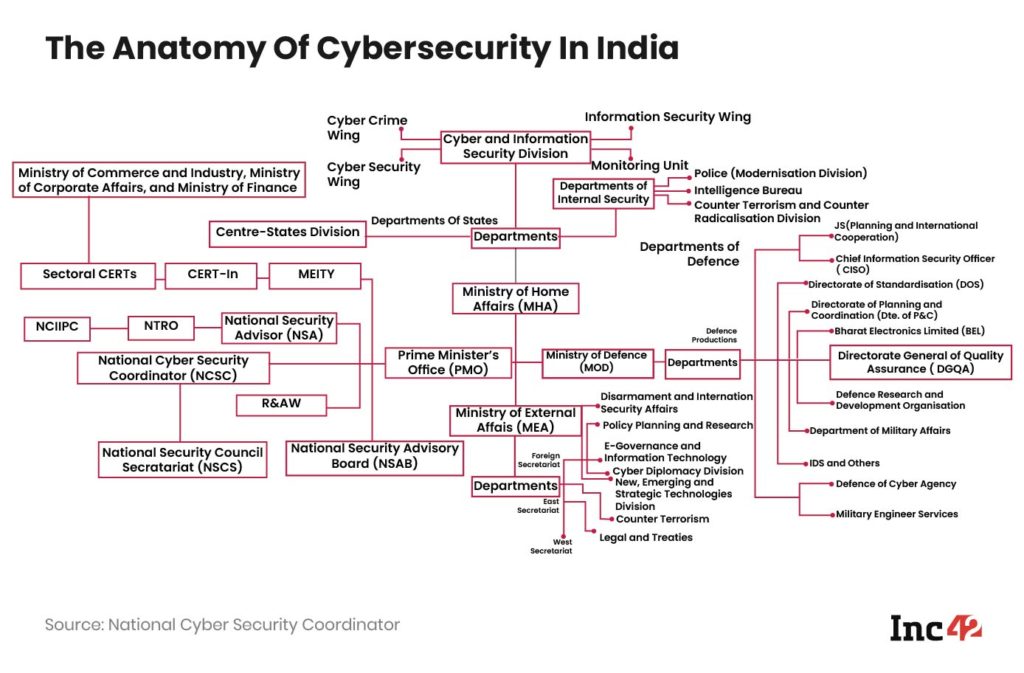
But on a broader policy level, the Indian government has already announced its plans to roll out the National Cyber Security Strategy 2020. In sync with this initiative, offence mechanisms come under the ministry of defence (military intelligence), the ministry of external affairs and the PMO (R&AW), while a large chunk of the cybersecurity defence mechanism is run by the Cyber And Information Security Division (C&IS) division under the ministry of home affairs.
In addition, The ministry of electronics and information technology runs the Indian Computer Emergency Response Team (CERT-In), a key nodal agency that deals with cyberattacks and other cybercrimes.
CERT-In has also signed MoUs with their global counterparts in eight countries – the UK, South Korea, Canada, Australia, Malaysia, Singapore, Japan and Uzbekistan. Interestingly, the ministry of external affairs had signed an MoU with the Shanghai Cooperation Organization (SCO), according to a statement released by the Indian government in 2016.
According to these MoUs, the organisations concerned have agreed to exchange cyber information regarding cyberattacks, phishing and hacking to ensure timely prevention of the same.

The Narendra Modi government has also set up a National Security Council chaired by himself and four other ministries — external affairs, finance, defence and home. The secretary-general of this council is the National Security Advisor, Ajit Doval.
Elaborating on this, National Cybersecurity Co-ordinator, Lt Gen. Rajesh Pant, said in an interview with the media portal, Medianama, “The aim is to advise this Council in overseeing and compliance of all cybersecurity aspects, including the implementation of cybersecurity action plans by the nodal agencies, the evaluation and analysis of incidents and then forming incident-response monitoring teams. There is a training part also. There is an aspect of international forums and providing consultation and guidance to state governments. And (one can) also engage with the private industry for the formulation of policies.”
The government is also planning to create a tri-service agency for cyberwarfare. This will see increased co-ordination among the stakeholders such as the defence cyber agencies and the national cybersecurity advisor. It will also include more than 1,000 experts.
The National Cybersecurity Co-ordinator’s office has also partnered with the Data Security Council of India (DSCI), the cybersecurity arm of the IT industry lobby NASSCOM, and launched a portal called TechSagar.
“To combat the growing threat from cybercrime, there is an urgent need to collaborate and develop cybertechnology capabilities in India. With the launch of TechSagar, we have sown the seed for startups to prosper in cybertech. This is a good example of the government facilitating industry growth in a strategic domain,” said Lt Gen. Pant.
How Indian Govt Has Misplaced Cybersecurity Priority
As part of the Indian government’s defensive and offensive mechanisms, a bulk of these initiatives are largely misplaced, believe several cybersecurity experts. Many of these initiatives have been implemented under the garb of dealing with cyberthreats but eventually help the government muzzle the opposing voices, protesters and others, whom the authorities want to ‘neutralise’.
In 2019, the Pegasus spyware from Israel caused a huge uproar worldwide. The spyware that secretly extracts a user’s private data, including passwords, contact lists, calendar events, text messages and even voice calls, targeted more than 1,400 people globally and 121 people in India, as confirmed by Facebook last year.
Interestingly, the NSO Group, the maker of the spyware, later clarified that the product was only sold to government authorities. It clearly underlines how invested governments are in tracking their own citizens without issuing any clarification or notification. The Indian government has also set up a Centralised Monitoring System (CMS) for ‘lawful interception’ and monitoring of mobile phones, landlines and internet traffic through mobile networks.
In March last year, the Modi government sought the call data records (CDRs) of all mobile subscribers residing in several pockets of the country. (Data was required for specific days of late 2019 and early 2020.) Later on, the incident was red flagged by telecom operators and it came to light that Delhi, Haryana, Punjab, Himachal Pradesh, Jammu & Kashmir, Madhya Pradesh, Odisha, Andhra Pradesh and Kerala had asked for this information.
Should such incidents ring a warning bell that global states are targeting their citizens more than the cybercriminals? Not necessarily. According to Pukhraj Singh, surveillance is the heart of cybersecurity and it is always challenging to limit essential technical exercises within the legal parameters as legal parameters are yet to catch up with the fast-changing technical parameters.
Speaking to Inc42 on the condition of anonymity, a cybersecurity expert strongly disagrees, saying that mass surveillance can never be the solution. In fact, it is the dumbest response to cyberthreats as it shows that the government is totally unprepared to handle such emergencies. Second, it clearly violates the Supreme Court’s judgement which recognised privacy as one’s fundamental right. This also includes internet privacy.
However, there are hundreds of cases where the authorities did not uphold these rights. The arrests of the climate change activist Disha Annappa Ravi, Dalit activist Nodeep Kaur, independent journalist Mandeep Punia and Rona Wilson, the public relations secretary of the Committee for Release of Political Prisoners (CRPP), who has been in jail for the past two years, are proof enough.
Granting bail to Disha Ravi, the Delhi High Court said:
“Citizens are conscience keepers of government in any democratic nation. They cannot be put behind bars simply because they choose to disagree with the State policies. The offence of sedition cannot be invoked to minister to the wounded vanity of the governments.”
The case of Rona Wilson, who was arrested as certain letters were found on his computer, has now become more intriguing. Arsenal Consulting, a Massachusetts-based digital forensics firm, has found through its forensic research that an attacker used a malware programme to infiltrate his laptop before his arrest and deposited at least 10 incriminating letters.
Moreover, the way the government has amended the draft Personal Data Protection Bill 2019 and introduced the ‘Intermediary Guidelines’, which not only curb a common person’s freedom but also bulldoze the intermediaries like WhatsApp, Signal and Telegram and most importantly, hinder the freedom of Press, clearly underlines what the government is focussing upon.
Quizzed on how India should tackle cyberattacks instead of curbing people’s cyberfreedom, Palmer of Tenable says that India’s needs are not different from the rest of the world when it comes to cybersecurity. When one looks at the vast majority of breaches that occur, whether they are in India or happening globally, most of these are caused by overlooking known vulnerabilities.
“At a very fundamental level, practising basic cyberhygiene such as patching systems and using strong authentication can significantly reduce the risk of compromise on critical networks. Doing so will ensure that organisations can identify vulnerabilities and exposures before they can be compromised. This allows organisations to make the necessary corrections to mitigate those weaknesses.”
Need- Of- The -Hour: Analyse And Automate
Commenting on the NCSC role, Pukhraj Singh says that word co-ordination in the natural course of co-ordination cannot proceed manually by sending notifications, pdf dispatches or emailing to stakeholder organisations.
“The co-ordination part itself needs to be automated. I am not sure if that has happened yet. There has to be a certain amount of automated analysis, especially across government networks, and that kind of understanding should be there across the whole spectrum of other organisational networks. The co-ordination part needs to be a bit automated.”
Similarly, CERT-In is an agency that handles the incident response for government organisations. “However, if you read the reports, the information is mostly derived from what the companies are providing to that agency. This should not be the case,” says Singh. “It (CERT-In) is basically working like an aggregation body. It is collecting data from other people or private intelligence firms. CERT-In supposed to have its own analytical capability. It is essential for the agency to understand what the adversary is up to.”
Another expert currently working with a government-run cybersecurity agency, concurs. Requesting not to be named, the person says, “There has been a clear lack of co-ordination among agencies. Unlike Israel, China and many other countries, the interaction among Indian agencies is far too less and that does not help. At the same time, some of these agencies (like ours) report to the MHA, while others report to the PMO, some others report to Defence ministry, MeitY etc. Initially, this was done for validation and creating separate sources. But unlike the US, which can afford this, we do not have the state-of-the-art infrastructure at every level or enough data to analyse. And, there is a great need for convergence”
With the NCSC in place, things are supposed to change. But considering the vicious nature of the cyberattacks that the country is facing, the pace is too slow, he adds.
Can the Indian government deal with these challenges and put its house in order in time? Can the government run surveillance programmes without violating people’s privacy?
Experts believe that there are multiple ways to tackle this challenge. The data can be processed anonymously by using blockchain and can be traced back to IP addresses as and when there is a red flag. But the question is: Is the government ready to do so or does it want to use muscle power for an easy way out?
The post The Anatomy Of Cyberwarfare: Is India Ready To Take On China? appeared first on Inc42 Media.
0 Comments